⚡Key Takeaways
- SaaS data security protects sensitive information in cloud-based software through proper access controls, encryption, and monitoring systems
- Common security risks include data breaches, unauthorized access, compliance violations, and human error with 75% of organizations experiencing SaaS-related incidents in 2024
- Essential best practices include implementing multi-factor authentication, regular security audits, data encryption, and establishing clear security policies
- Choosing embedded analytics that deploy to your cloud eliminates third-party security concerns while maintaining complete data control
Shipping fast in SaaS can come at the cost of security. And the longer you wait, the worse it gets: more data, tenants and risk. More than being just a dev problem, SaaS data security is a product problem, a customer problem, a revenue problem.
Failures destroy customer trust, trigger regulatory fines, and can sink entire companies overnight.
In this guide, we’ll help you rethink your approach. You’ll learn how to embed security where it matters: inside your data model, analytics layer, and self-service tools. The result would be a platform that scales with confidence and earns customer trust without killing momentum.
What is SaaS Data Security?
SaaS data security encompasses all policies, technologies, and processes that protect sensitive information stored within cloud-based software applications.
Think beyond passwords and firewalls. Data security in SaaS apps means controlling who accesses what information, when they can access it, and what they can do with it.
SaaS security covers everything from identity management to data encryption both at rest and in transit. It includes monitoring for cyber threats, ensuring regulatory compliance, and having incident response plans ready when problems arise.
The key difference between traditional security and SaaS security lies in shared responsibility. While SaaS providers handle infrastructure security, you’re still responsible for configuring access controls, managing user permissions, and protecting your data within their systems.
The Importance of SaaS Data Security
Your customers don’t just use your product but trust it with their business. That trust hinges on one thing: how well you protect their data.
Lose that, and you’re not just looking at churn but risking collapse.
It’s no longer a question of if your SaaS platform will be targeted. It’s already happening. A staggering 75% of organizations experienced a SaaS-related security incident in the past year, a 33% increase over 2024.
Even more unsettling is the fact that 89% of them believed they had “appropriate visibility” at the time of the breach.
Breaches hurt your infrastructure and erode brand. The average cost of a breach now exceeds $4.88 million globally, but the long-tail effects (legal battles, customer loss, and damaged investor confidence) can cripple growth for years.
Here’s why SaaS data security is under siege:
- Compliance requirements like GDPR, HIPAA, and SOC 2 are mandatory for doing business with enterprise customers
- Cyber attacks specifically target SaaS applications because they contain concentrated customer data across multiple organizations
- Data sprawl across multiple SaaS vendors creates an expanded attack surface that’s harder to monitor and secure
- Remote work has increased reliance on SaaS apps, making identity security more complex than ever
Important: Security gets exponentially harder to fix the later you address it. Companies with proper multi-tenant architecture planning from the start avoid many common security pitfalls that plague organizations trying to retrofit security measures.
Our FREE guide covers real-world ways to build security into your product’s analytics layer before it becomes a liability. Download it here to get ahead of security risks.
Common SaaS Data Security Risks and Challenges
70% of companies now running dedicated SaaS security teams means the threats are no longer theoretical.
Even platforms that look polished have webs of APIs and third-party data flows under the hood. Add multi-tenant analytics to the mix, and the risk multiplies.
Here are five of the most costly SaaS security risks you’ll want to mitigate early.
Unauthorized Access and Account Takeover
Identity credentials remain the weakest link in most SaaS security implementations.
As Eric Schwake, Director of CyberSecurity Strategy at Salt Security, points out: “As APIs are now touching this data more than ever, it’s essential to understand how they utilize it and promptly identify any potential risks.”
Account takeover attacks increased by 307% under two years, with hackers targeting SaaS apps because they provide access to multiple customer datasets at once. Single sign-on solutions help but only when configured correctly with proper identity providers.
Data Loss and Information Sprawl
Your data doesn’t stay in one place anymore.
One team exports reports from your analytics platform, another syncs it to a CRM, and marketing pulls a version into their own personalized dashboard tools. Then it gets emailed, duplicated, downloaded, and often forgotten.
This data sprawl makes it nearly impossible to track where sensitive information lives or who has access to it.
A self-service dashboard built for execs might include embedded queries from a data warehouse, personalized fields from a CRM, and free-form notes from customer success, all of which get cached, shared, or misused across tenants.
Traditional data loss prevention (DLP) tools, designed for static environments, can’t keep up with this fluid reality.
Shadow SaaS and Unmanaged Applications
It starts small: a sales manager signs up for a productivity tool to speed up reporting or the data analyst connects a free dashboard plugin to visualize monthly KPIs. Soon, dozens of unsanctioned apps are quietly handling customer lists and forecasts, all without the knowledge of your IT or security team.
This Shadow SaaS creates security blind spots that security teams can’t monitor or protect.
Each app brings its own permissions model, API exposure, and data handling quirks. Even “approved” tools become risk vectors when employees connect them to unvetted third-party plugins, automation bots, or integrations that weren’t built with security in mind.
Inadequate Compliance Monitoring
Regulatory compliance requirements change constantly, but many organizations only check their SaaS security posture annually during audits.
Without continuous compliance monitoring, you’re flying blind for most of the year. That gap creates the perfect storm for unnoticed violations, data exposure, and broken trust.
For example, Business Associate Agreements (BAAs) in healthcare demand real-time oversight and demonstrable controls every single day. So when alerts are buried in logs or audit trails stitched together at the last minute, it becomes a liability.
Human Error and Misconfiguration
One overlooked setting, a rushed permission change, an outdated user role. That’s all it takes to open the floodgates. Employees accidentally share sensitive files, misconfigure permissions, or fall victim to phishing attacks.
Configuration drift happens gradually as team members make small changes without understanding the security implications. What starts as proper access controls slowly becomes a security nightmare.
Compliance & Regulatory Considerations
The point of compliance is proving to your users, especially in enterprise and regulated industries, that you can be trusted with their data. Because when customers ask about GDPR or SOC 2, what they’re really asking is: “If something goes wrong, will you protect me?”
Plus in multi-tenant environments, a single security gap can ripple across every customer you serve.
Let’s break down the biggest compliance frameworks and why they matter to your product, roadmap and reputation:
- GDPR (General Data Protection Regulation)
Who it affects: Anyone handling the data of EU citizens, regardless of company location.
Why it matters: GDPR isn’t optional. You need to offer users data deletion rights, clear opt-ins, and notify them within 72 hours if there’s a breach. If your product doesn’t support these by design, you’re risking customer trust.
- HIPAA (Health Insurance Portability and Accountability Act)
Who it affects: SaaS platforms working with healthcare data or patients in the U.S.
Why it matters: HIPAA violations are criminally prosecutable. If you’re collecting or analyzing medical data, you need to implement safeguards, sign Business Associate Agreements (BAAs), and ensure your vendors do the same. Yes, even your healthcare analytics platform must comply.
- SOC 2 Type II
Who it affects: Any SaaS company selling to enterprise clients.
Why it matters: SOC 2 reports cover five pillars: security, availability, processing integrity, confidentiality, and privacy. They take ~9 months to implement properly but large clients won’t even consider signing without it. It’s the price of admission for enterprise sales.
- PCI-DSS (Payment Card Industry Data Security Standard)
Who it affects: Anyone handling or displaying credit card data even if it’s just masked digits in a report.
Why it matters: Credit card data comes with a trail of responsibility. If your dashboard shows payment info, you’re part of the compliance chain. And so are your vendors. One weak link can compromise the whole chain.
So if you’re building SaaS, don’t treat compliance as an afterthought. Bake it into your architecture, workflows, and even your analytics layer. The companies that do close deals faster and reduce legal risk.
Best Practices for SaaS Data Security
What works in the real world versus what sounds good in theory? These SaaS security best practices come from companies actually managing complex environments at scale.
Implement Zero Trust Architecture
Zero trust means never trusting any user or device by default, even inside your network perimeter. Every access request gets verified through identity management systems before granting permissions.
Start with multi-factor authentication across all SaaS applications. Two-step authentication reduces automated attacks by 99.9% but only works when enforced consistently. Microsoft Entra ID and similar identity providers make this easier to manage at scale.
Also, configure single sign-on with proper SSO services that support modern security protocols. This way, employees get seamless access while IT maintains central control over identity credentials.
Establish Data Classification and Governance
A billing system storing encrypted payment tokens doesn’t require the same level of access controls as an internal reporting dashboard. Yet many teams apply uniform safeguards across the board, wasting resources in low-risk zones while leaving high-risk areas dangerously exposed.
To fix that, start by mapping your data lifecycle, where data moves.
- Where is customer data created?
- When is it processed?
- Who touches it?
- How is it stored, archived, or deleted?
Without these answers, security policies become guesswork and compliance audits turn into fire drills.
Architecture plays a big role here. Choosing the right security model determines how easily you can enforce policies, prove compliance and recover from threats.
For instance, Qrvey’s inheritance-based security model enforces granular permissions at the user, data, and tenant level.
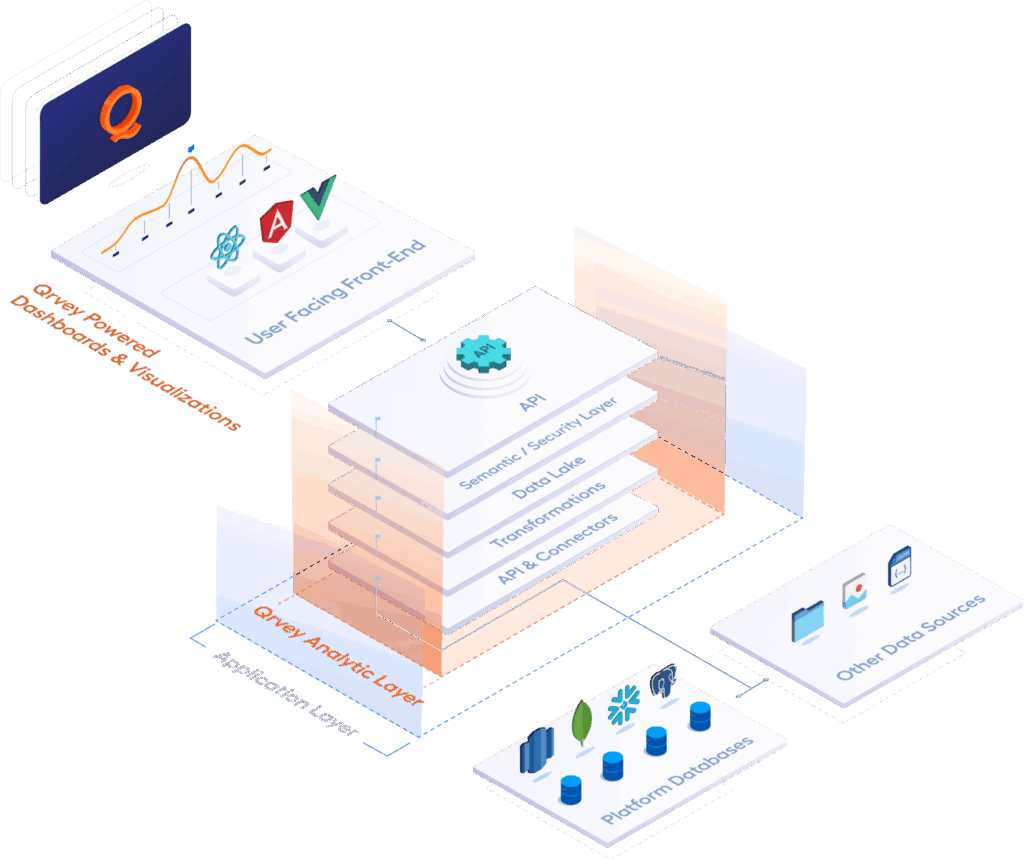
Combined with its native data lake architecture, teams can enforce smart, scalable protections without rebuilding their architecture from scratch.
Deploy Automated Protection and Monitoring
As your platform scales, so does your attack surface: more endpoints, more integrations, and more chances for something to go wrong.
Security information and event management systems provide the visibility you need to detect threats early. SaaS security posture management platforms specifically designed for cloud environments catch misconfigurations before they become vulnerabilities.
Threat detection works best when combined with automated response. Because when something suspicious triggers an alert, you can’t afford to wait on a manual ticket queue.
Automated protection tools take immediate action and escalate only what truly needs human review.
Secure Third-Party Integrations
Third-party risk isn’t a box you check once. It’s a living threat vector. A vendor’s SOC 2 certification might look great today, but what about after their next software update? Continuous monitoring, not just annual audits is what keeps you ahead of compromise.
Then there’s the overlooked issue of embedded analytics, often deployed through iframes. Sure, they simplify integration. But without understanding iframe sandboxing, cross-origin policies, and secure recovery paths, you’re trading speed for exposure.
It’s why tools like Qrvey use JavaScript-based widgets and a fully native API layer.
So you have total control over how analytics are embedded, secured and personalized for each tenant.
Implement Comprehensive Backup and Recovery Plans
Most SaaS teams assume disaster recovery is the cloud provider’s problem. After all, infrastructure uptime is covered, right?
But when ransomware hits or a user accidentally wipes out a table, AWS won’t restore your customer’s dashboard or undo corrupted reports.
Multi-tenant security means precision. You need granular restore capabilities that can isolate and recover individual tenant data without compromising others. And you need cyber recovery strategies that account for increasingly sophisticated threats targeting both live systems and backups.
Secure Your Data Today with Qrvey’s Embedded Analytics
Traditional SaaS providers promise powerful analytics but at the cost of handing off your data. With Qrvey, you don’t have to choose.
Our embedded analytics platform lives inside your cloud, not someone else’s. That means no compliance gaps or extra API exposure. Your existing security stack handles everything from access control to encryption and monitoring. Multi-tenant architecture is also already accounted for.
Instead of forcing trust, Qrvey builds on the systems you already trust. Companies using our data platform report faster compliance audits because they don’t need to verify third-party security practices.
Want faster audits, cleaner compliance and zero anxiety? Request a demo for free and see how it feels

David is the Chief Technology Officer at Qrvey, the leading provider of embedded analytics software for B2B SaaS companies. With extensive experience in software development and a passion for innovation, David plays a pivotal role in helping companies successfully transition from traditional reporting features to highly customizable analytics experiences that delight SaaS end-users.
Drawing from his deep technical expertise and industry insights, David leads Qrvey’s engineering team in developing cutting-edge analytics solutions that empower product teams to seamlessly integrate robust data visualizations and interactive dashboards into their applications. His commitment to staying ahead of the curve ensures that Qrvey’s platform continuously evolves to meet the ever-changing needs of the SaaS industry.
David shares his wealth of knowledge and best practices on topics related to embedded analytics, data visualization, and the technical considerations involved in building data-driven SaaS products.
Popular Posts
Why is Multi-Tenant Analytics So Hard?
BLOG
Creating performant, secure, and scalable multi-tenant analytics requires overcoming steep engineering challenges that stretch the limits of...
How We Define Embedded Analytics
BLOG
Embedded analytics comes in many forms, but at Qrvey we focus exclusively on embedded analytics for SaaS applications. Discover the differences here...
White Labeling Your Analytics for Success
BLOG
When using third party analytics software you want it to blend in seamlessly to your application. Learn more on how and why this is important for user experience.